Data Logging Using Syslog
The ENVIROMUX Mini Environment Monitoring System logs data from its sensors, and sends it to a computer using Syslog.
Data Logging Using Syslog
| The ENVIROMUX Mini Environment Monitoring System stores event and data entries in the system data log. The system data log can be downloaded as a tab-delimited plain text file, viewed via the web interface, or sent to up to 16 remote IP addresses using syslog. Data logging using Syslog on a remote computer allows for historical data collection in a convenient location. Linux/Unix-based computers use a standard syslog daemon to accept log data from the kernel, from any and all local processes, and even from processes on remote systems. Syslog support is not included on Windows-based computers, and will need a third-party application to accept the syslog alerts from the ENVIROMUX-MINI-LXO. |
|||
Configuring the ENVIROMUX-MINI-LXO for Syslog |
|||
| The ENVIROMUX-MINI-LXO is easily configured to send log data to a syslog server, and attached sensors can be individually selected on/off to ensure that unneeded data is not sent. Access the sensors individually within the web interface by clicking on "Monitoring", and then "Summary" menu links to the left. Each sensor status has an "Edit" button on the right for additional configuration options. Click the "Edit" button for the desired sensor, expand the "Alert Settings", "Non-Critical Alert Settings" and/or "Critical Alert Settings". Checkmark "Enable Syslog Alerts" in the sensor configuration menu. Expand the "Data Logging" tab, checkmark "Add to data log" and set the desired logging period, then click "Save" to select the sensor for sending syslog alerts. |
|||
Example sensor syslog settings: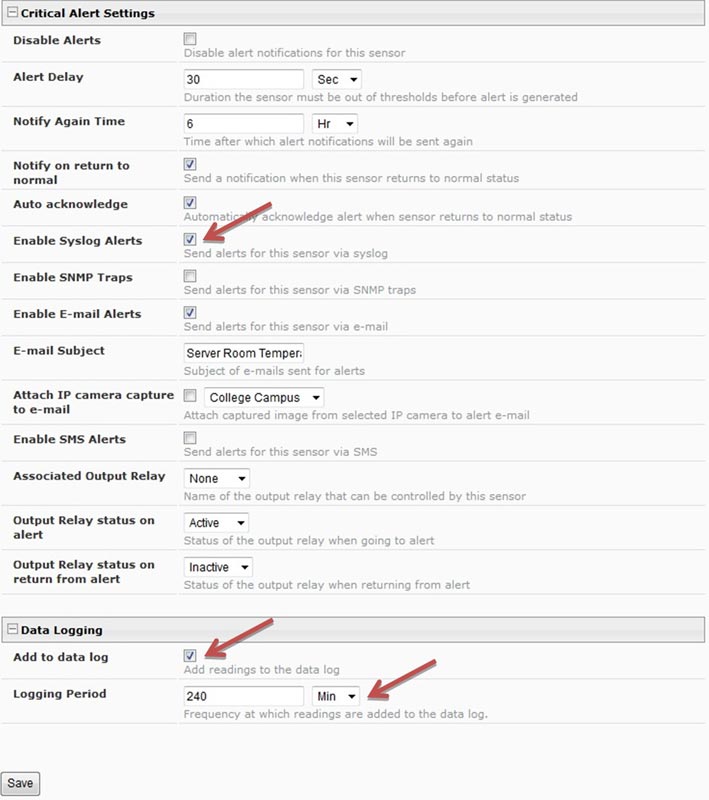
|
|||
| Next, the ENVIROMUX-MINI-LXO needs to be configured for sending the syslog alerts to up to 16 users/IP addresses. Click "Administration" menu link on the left, followed by "users" in the submenu that appears to access the user settings. Click on each user/IP address that needs to receive syslog alerts, expand the "Contact Settings" tab, and checkmark "Syslog Alerts". Under "Syslog/SNMP IP Address", enter the IP address for the user to receive the alerts, and click "Save" to save the settings. Ensure that the user's checkmarked Group(s) correspond to the correct Sensor Groups in order to receive Syslog Alerts: e.g. if the temperature sensor sends notifications to Group 1 and the user should receive alerts, checkmark Group 1 under the user settings. Enter this information for up to 16 of the users to receive syslog alerts. | |||
Example user syslog settings: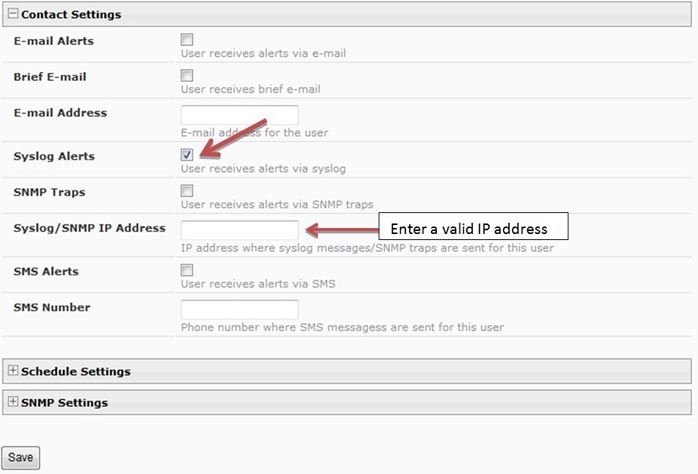
|
|||
| Last, the datalog needs to be configured to enable remote syslog logging of alerts. Select the "Log" menu link on the left and click on "Log Settings" in the drop down list. Expand the "Data Log Settings" tab, select the applicable Group number(s), then checkmark "Enable Syslog Alerts" and "Enable Syslog Remote Logging". Click "Save" to save the settings. | |||
Example data log settings: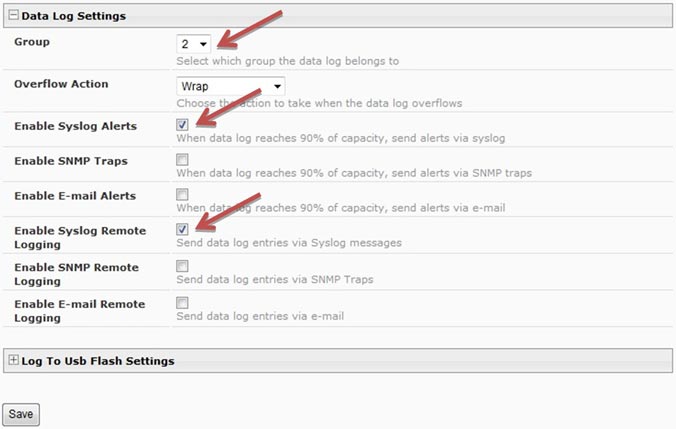
|
|||
Configuring a Windows-based Syslog Server to Receive Syslog Alerts |
|||
|
Windows-based computers do not include native syslog support, and will need a third-party application such as Kiwi Syslog (available as freeware with 30-day advanced options free trial) to receive syslog alerts. The software can be installed either as a stand-alone application, or installed as a service running uninterrupted in the background. Installing the software as a service doesn't require the user to login to Windows to accept syslog messages. Example Operating Mode: 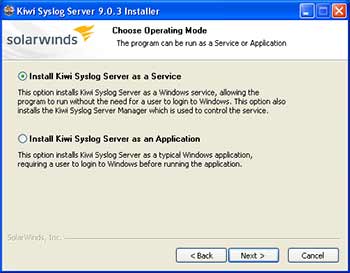 Once installed, the software can be setup to filter syslog alerts by priority and facility. In the Service Manager window, click the "File" menu, and then "Setup" to access the settings for the software. Right click the "Filters" submenu underneath "Default" in the "Rules" section of the menu, and click "Add filter". Rename the new filter accordingly, and hit enter to apply the name. Click the new filter's name to access the settings for that filter. Select "Priority" from the "Field" drop down list above to bring up the options for filtering incoming syslog messages. The chart shown categorizes each facility to the left, and priorities on the top. Since the ENVIROMUX-MINI-LXO sends messages as the "local0" facility, sroll near the bottom of the facility list to the left to find "local0" and select the priorities to filter. Click the green tick button at the bottom of the screen to set priorities. A match on each priority causes the filter result to be true, delivering the message. Setting a green tick in all of the priority values ensures a match will occur no matter what the message priority value. Example Priority and Facility Filter: 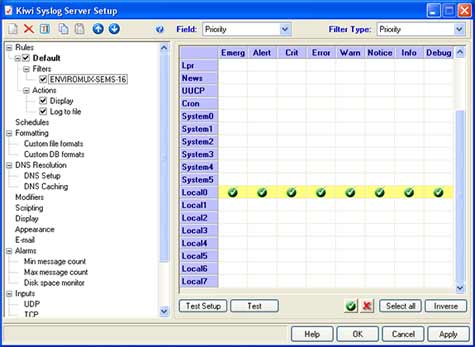 Click "Apply" to accept the settings, and "OK" to exit the Setup window. The default settings on the other options in the Setup window can be modified to fit individual needs of the user, but of particular importance is the "UDP" menu item under "Alarms". These default settings are standard remote message settings for syslog, and should not be changed. Example UDP Settings: 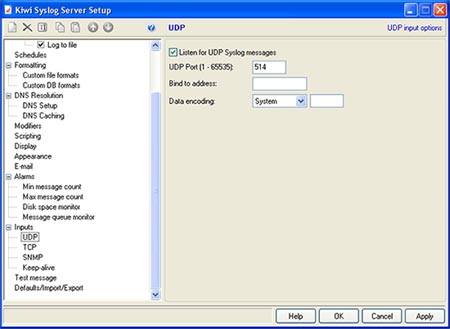 The software should now be ready to accept incoming syslog messages from the ENVIROMUX-MINI-LXO. Configuring the Linux/Unix-based Syslog Server to Receive Syslog AlertsThe standard syslog daemon used by Linux/Unix-based systems is configurable to accept alerts from remote systems. To configure the system to receive these alerts, two configuration files will need to be edited: /etc/sysconfig/syslog (/etc/init.d/sysklogd on some systems) and /etc/syslog.conf (/etc/rsyslog.conf on some systems).The security settings of the Linux/Unix-based syslog server may need to be configured to allow remote syslog alerts to be received. The default settings for the centralized syslog configuration file do not listen for remote messages, and will need UDP port 514 opened to accept remote UDP logging. On most systems, the "SYSLOGD_OPTIONS" (or just "SYSLOGD" on some systems) variable in the /etc/sysconfig/syslog (or /etc/init.d/sysklogd) file will need an "-r" included in it to open the port. Example syslogd configuration:
Save the changes to the syslogd configuration, and restart syslog to apply the changes. Example restart syslog command:
The system firewall may also need to have port 514 opened as well. Filtering Received Syslog AlertsAt this point, the received syslog messages are being written to the same file as many other system messages and alerts. Syslog writes each type of message received based on the settings in the /etc/syslog.conf (/etc/rsyslog.conf on some systems) configuration file. The syslog configuration file can be modified to isolate the messages coming from the ENVIROMUX-MINI-LXO for easier access. The file consists of two columns, first listing the facilities and severities of messages, and the second listing the files to which they should be logged. By listing the full path to a filename as a line's action in syslog.conf, messages that match that line will be appended to that file.Supported facilities in Linux are auth, authpriv, cron, daemon, kern, lpr, mail, mark, news, syslog, user, UUCP and local0 through local7. By default, the ENVIROMUX-MINI-LXO sends syslog messages as the "local0" facility. The example syslog.conf configuration below filters the incoming "local0" facility messages sent by the ENVIROMUX-MINI-LXO into two files. In this example, "local0" facility messages with the priority of informational are logged in the /var/log/syslog file, while "local0" facility messages with a priority of notice and higher are logged in the var/log/syslog.alert file for easy access. Example syslog.conf file configuration
Restart syslog again to apply the changes. |
